To Stop AI-Powered Adversaries, Defenders Must Fight Fire with Fire
Despite the revolutionary agentic delivery mechanism used to achieve groundbreaking speed and scale in this attack,…
Despite the revolutionary agentic delivery mechanism used to achieve groundbreaking speed and scale in this attack,…
The outcomes that matter most — speed, accuracy, cost, and real-time risk reduction — can only…
Gone are the days when Skype was the go-to VoIP tool for every chat, call, or…
Zero-Day Vulnerability in Windows Kernel When successfully exploited, attackers can gain SYSTEM privileges by winning a…
The Leader in Identity Security Innovation The breadth of CrowdStrike’s detection capabilities is also highlighted: “Falcon…
There’s no doubt that Skype was once one of the most popular instant messaging and video…

These reports include:With Falcon Cloud Security data correlated in Falcon Next-Gen SIEM, teams can detect cross-domain…
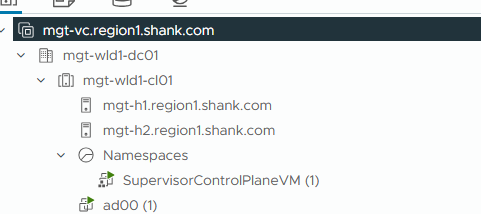
November 7, 2025 vCenter Supervisor Management is Blank Enabling / Disabling Supervisor Management Errors The Issue?…

The “404 Not Found” error during upgrade occurs when your system attempts to download packages from…
Key capabilities:Using the single Falcon sensor, organizations can move from deployment to complete XIoT visibility in…
While these agents can expedite individual tasks, their ultimate potential is realized when they operate in…
This blog includes descriptions of products, features, or functionality that may not be currently generally available….
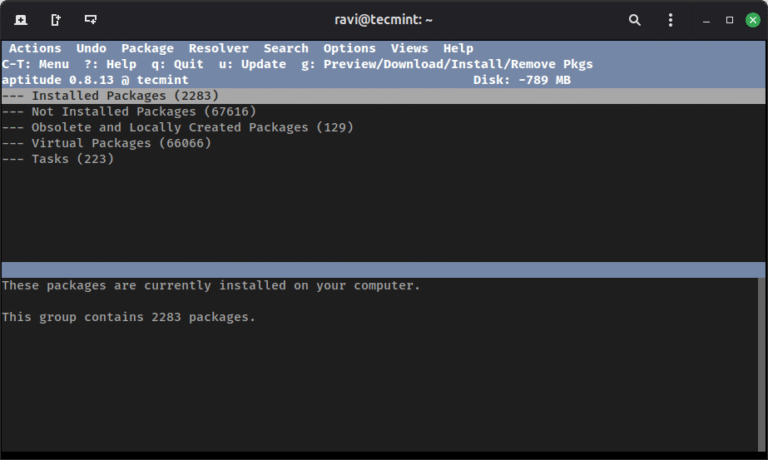
Debian offers several tools for managing software packages, each serving a specific purpose in the package…
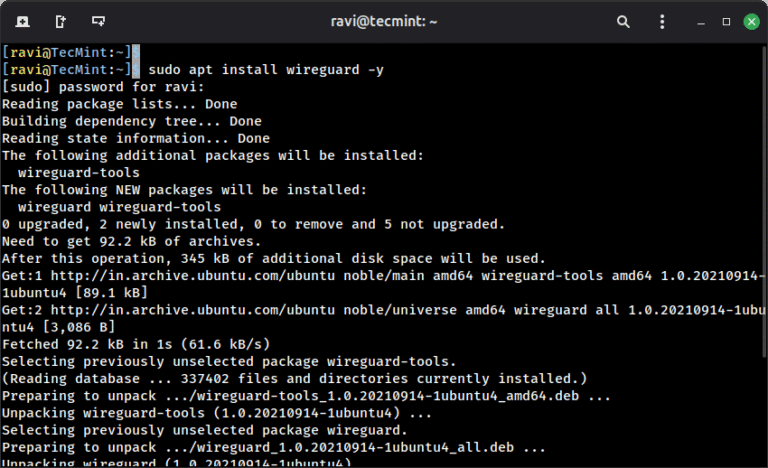
When you connect to a coffee shop’s WiFi or access the internet from any public network,…
In terms of methodology, voice phishing and fake CAPTCHA pages have become key enablers for gaining…