Under the Hood: How It Works
Step 3: Dynamic behavioral analysis
Step 5: Similar sample identification
The agent triggers CrowdStrike’s secure sandbox to execute the file in a controlled environment, where it captures runtime behavior including network communications, file system modifications, registry changes, and process interactions.
Once triggered, the agent kicks off retroactive threat hunting and deploys monitoring rules, while executing countermeasures such as isolating affected systems, exporting IOCs, and blocking command-and-control (C2) infrastructure.
Step 6: Summarization of findings
Step 7: Action
When the “Suspicious file QuickScan Pro” analysis prevention policy is enabled, the Falcon sensor automatically flags potentially suspicious files based on behavioral heuristics and machine learning models, then securely uploads them to CrowdStrike’s cloud.
This orchestrated approach replaces hours of manual analysis with an automated workflow that delivers expert-level insights in minutes, enabling security teams to handle higher alert volumes while maintaining consistent analysis quality.
Using malware search index capabilities, the agent performs content-based analysis to find related malware samples in CrowdStrike’s repository (over 8.5 billion samples), where it compares code structure and behavioral patterns to identify variants and related families.
The system matches observed characteristics against CrowdStrike’s YARA rule repository to identify specific malware families and variants.
Step 2: Initial static analysis and enrichment
Powered by a multi-tool architecture that runs without human intervention, the agent compresses hours of investigation into minutes and synthesizes the outputs into a consolidated report with malware family classification, threat level, behavioral summaries of key capabilities, related threat actor context, and clear remediation recommendations.
Below is a breakdown of that process:
Figure 2. The Malware Analysis Agent orchestrates multiple specialized tools to deliver comprehensive threat intelligence in minutes.
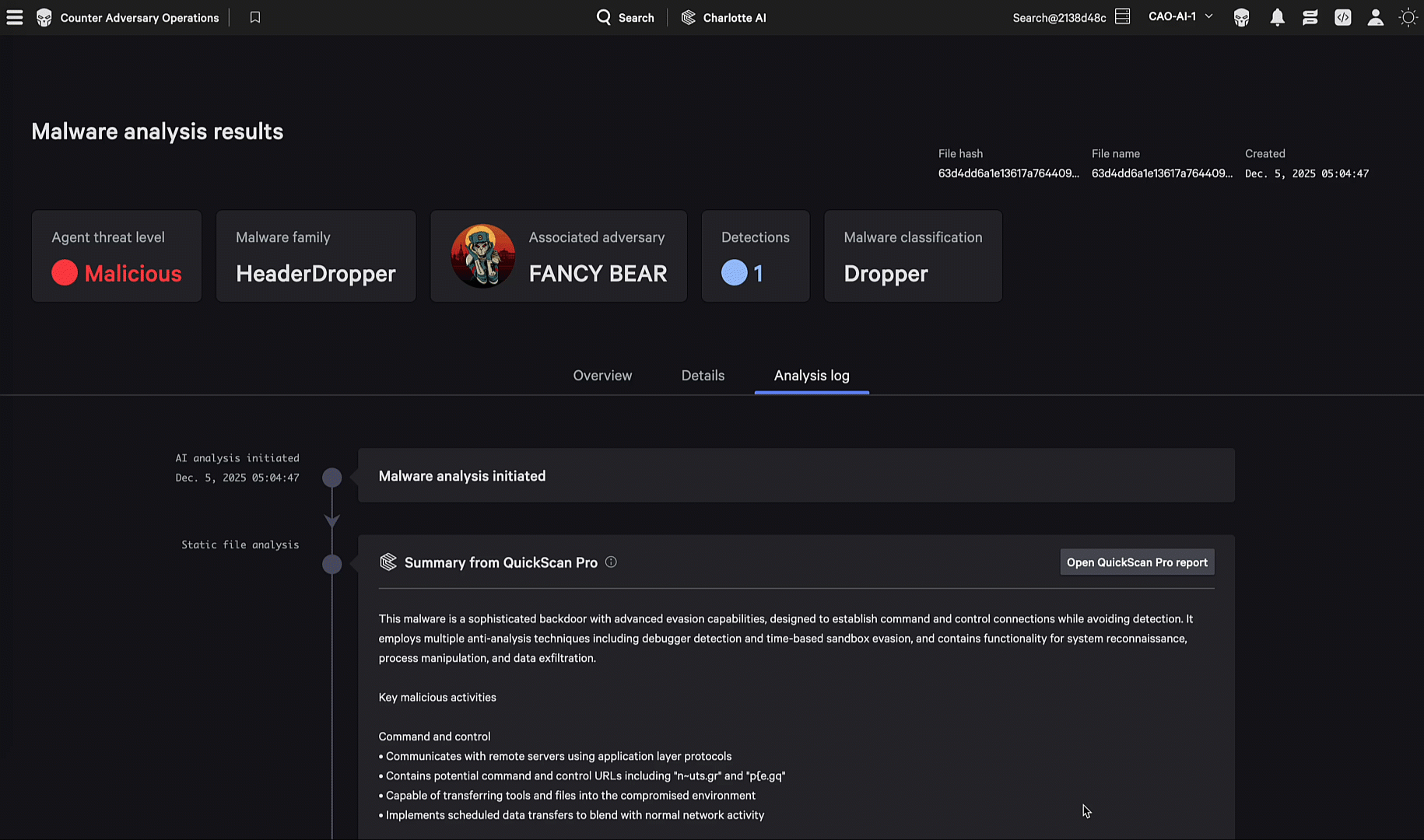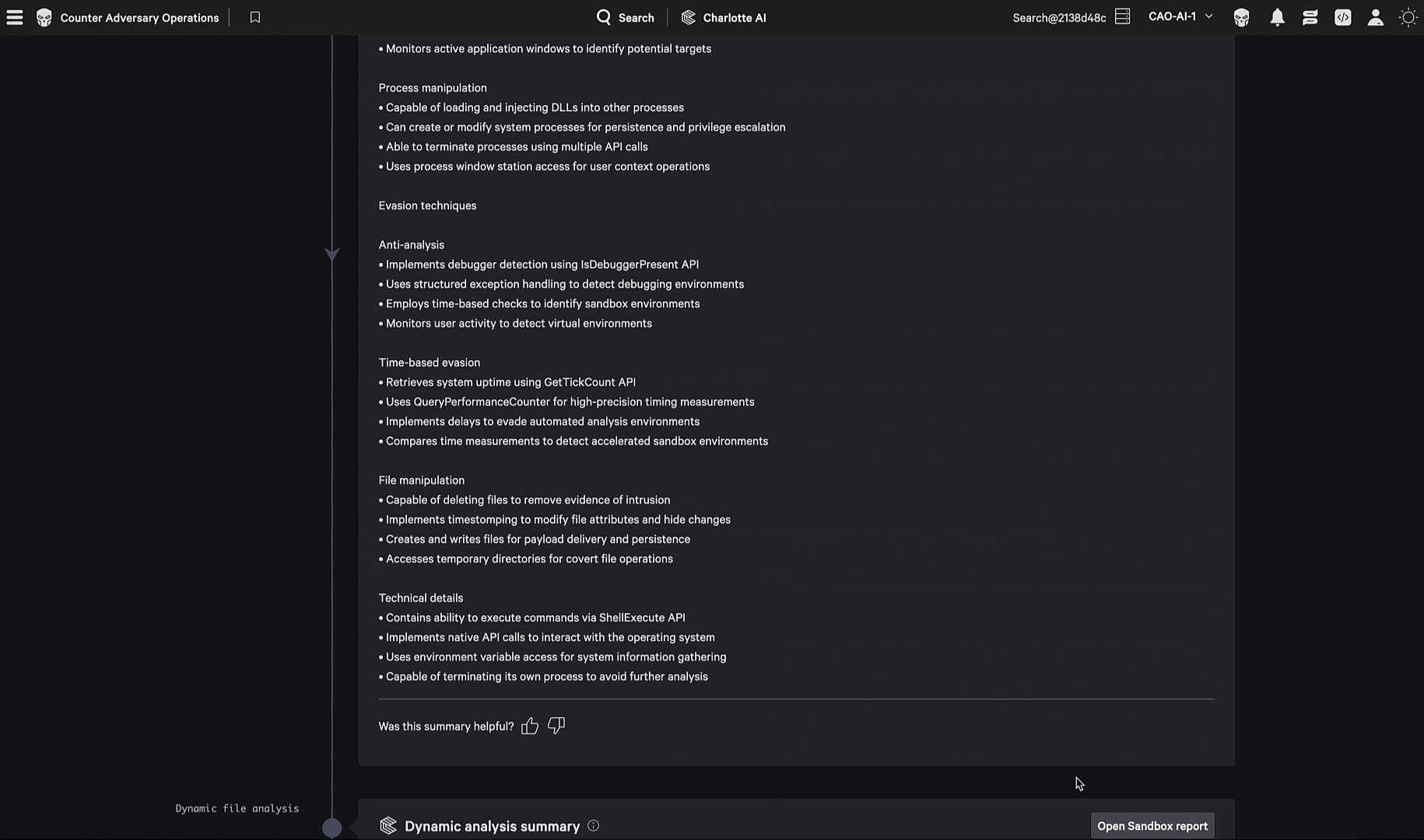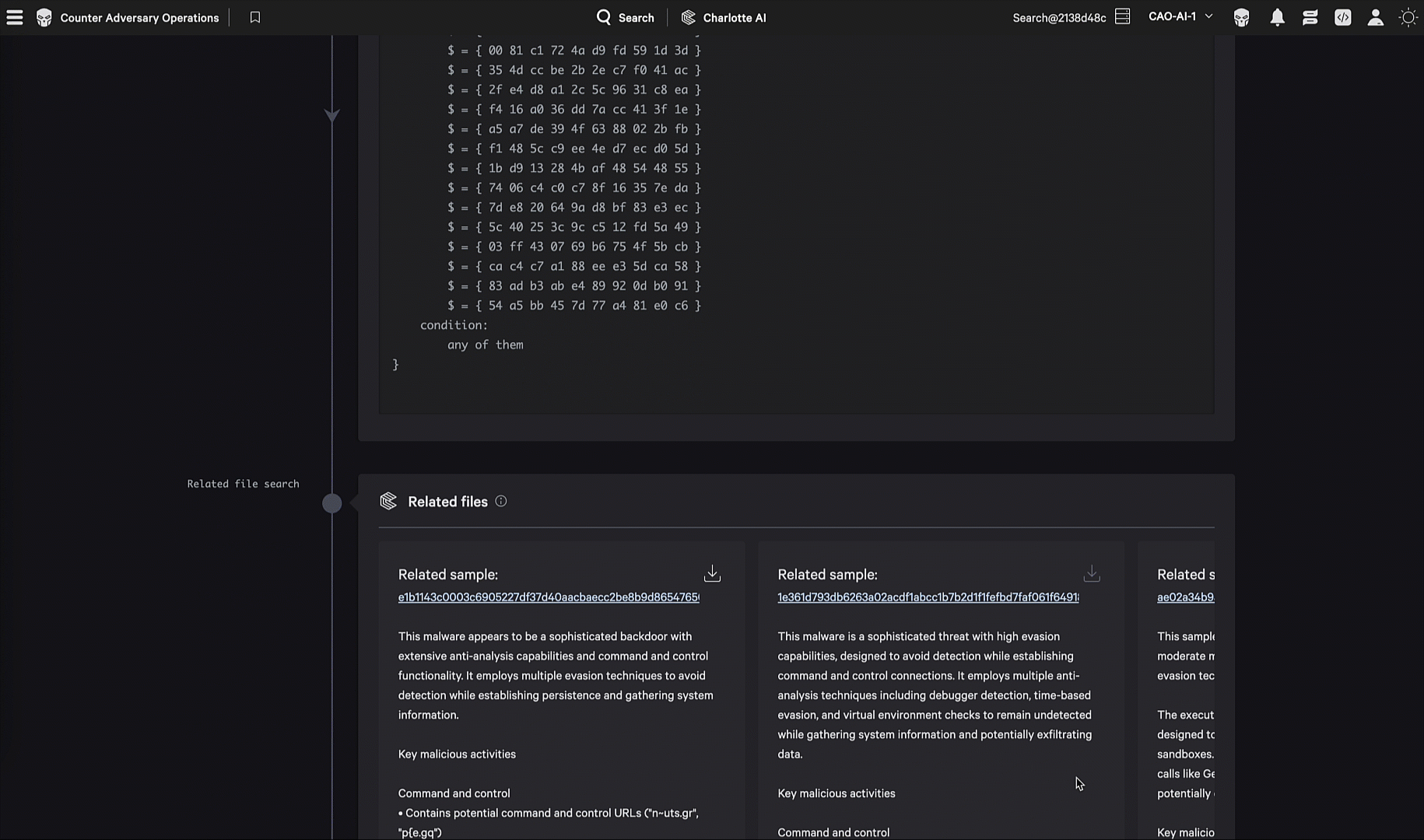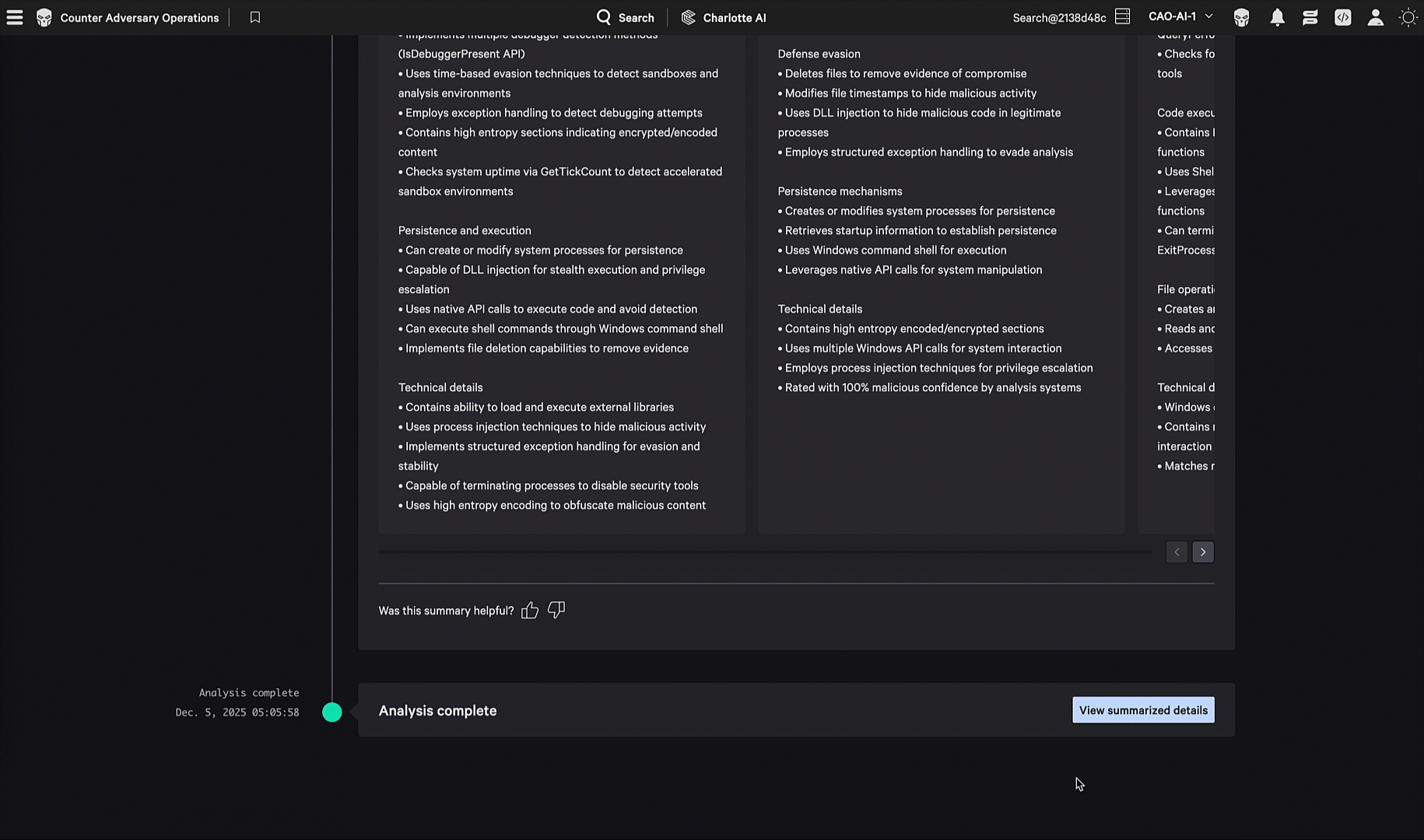
The agent then synthesizes findings from every stage into a unified report with confidence-scored classifications, behavioral summaries, and remediation recommendations.
The agent then performs rapid static analysis to examine file structure, embedded strings, and code patterns. At the same time, the system queries CrowdStrike’s threat intelligence database to enrich the analysis with information about similar files, known campaigns, and threat actor attribution.
The agent then coordinates analysis across multiple tools, performing static and dynamic analysis in parallel. It examines the file’s structure and code patterns, detonates the file in our secure sandbox to observe runtime behavior, identifies similar samples within our extensive malware repository, and matches patterns against CrowdStrike’s extensive signature database of over 5,000 YARA rules.
Step 4: Pattern matching and classification
The Malware Analysis Agent replaces the manual process of analyzing malware with a single orchestrated workflow, automatically kicking off deeper investigation whenever a suspicious file is identified.
Step 1: Automated file identification and upload