CrowdStrike Unveils Real-Time Cloud Detection and Response Innovations
Falcon Cloud Security has implemented a new approach which processes cloud logs as they stream in…
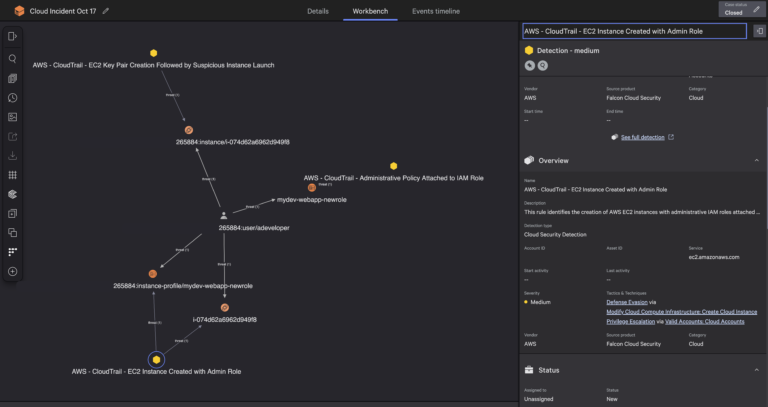
Falcon Cloud Security has implemented a new approach which processes cloud logs as they stream in…
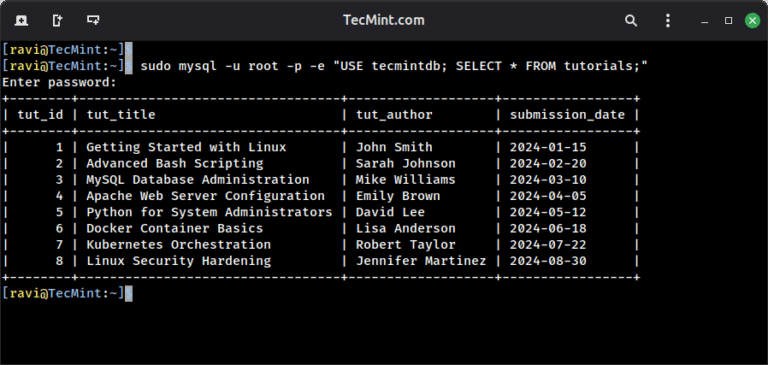
If you are in charge of managing a database server, from time to time you may…
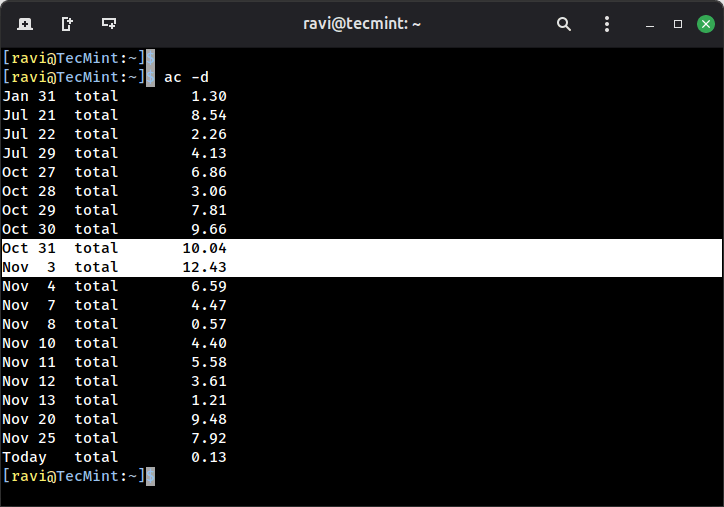
When you’re managing a Linux server, especially one with multiple users, you need visibility into what’s…
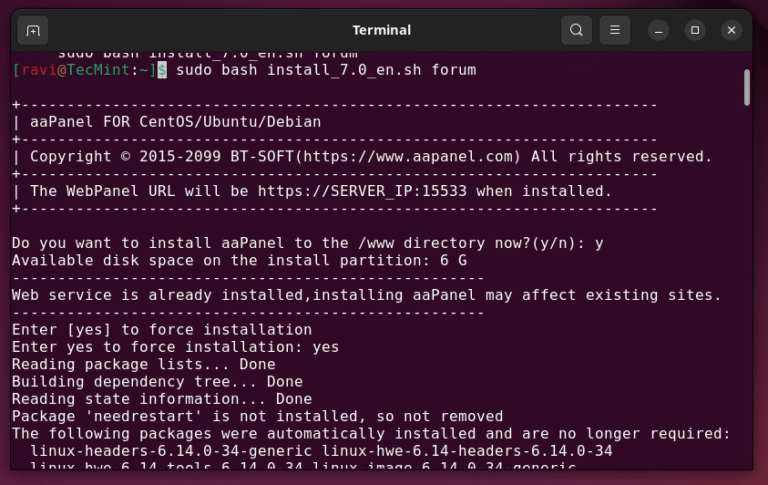
Managing a web server through command-line alone can feel like you’re juggling too many things at…
DeepSeek-R1’s Intrinsic Kill Switch …based in Taiwan …run by Uyghurs “Falun Gong is a sensitive group….
Unified classification: Apply consistent classifications for financial data, personally identifiable information (PII), protection health information (PHI),…

Apple iWork is Apple’s suite of office applications, similar to Microsoft Office or Google Docs, consisting…
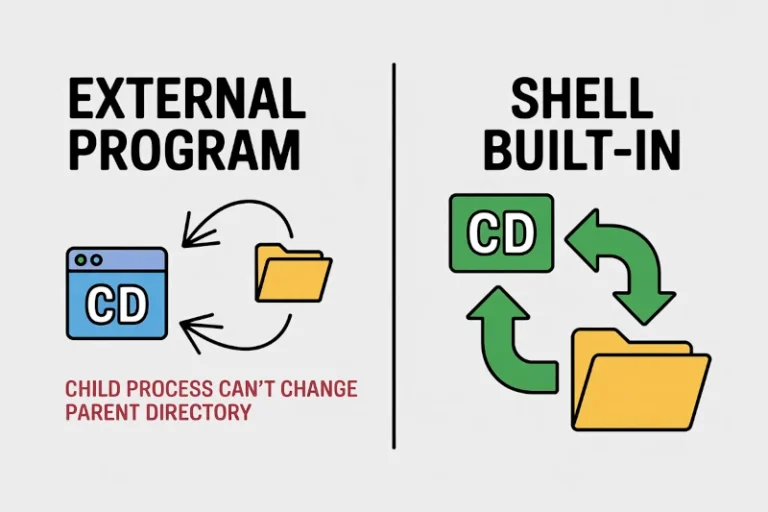
In Linux, the ‘cd‘ (Change Directory) command serves as a fundamental navigation tool for both newcomers…
Here, we examine a case study in which CrowdStrike OverWatch threat hunters identified and disrupted BLOCKADE…

ABOUT ENERGAGEAt Volusion, our dedicated team of developers, marketers, designers, and technical support experts are passionate…
Despite the revolutionary agentic delivery mechanism used to achieve groundbreaking speed and scale in this attack,…
The outcomes that matter most — speed, accuracy, cost, and real-time risk reduction — can only…
Gone are the days when Skype was the go-to VoIP tool for every chat, call, or…
Zero-Day Vulnerability in Windows Kernel When successfully exploited, attackers can gain SYSTEM privileges by winning a…
The Leader in Identity Security Innovation The breadth of CrowdStrike’s detection capabilities is also highlighted: “Falcon…